Multi-Vender MPSK deployment with Dynamic VLAN Assignment on FreeRadius
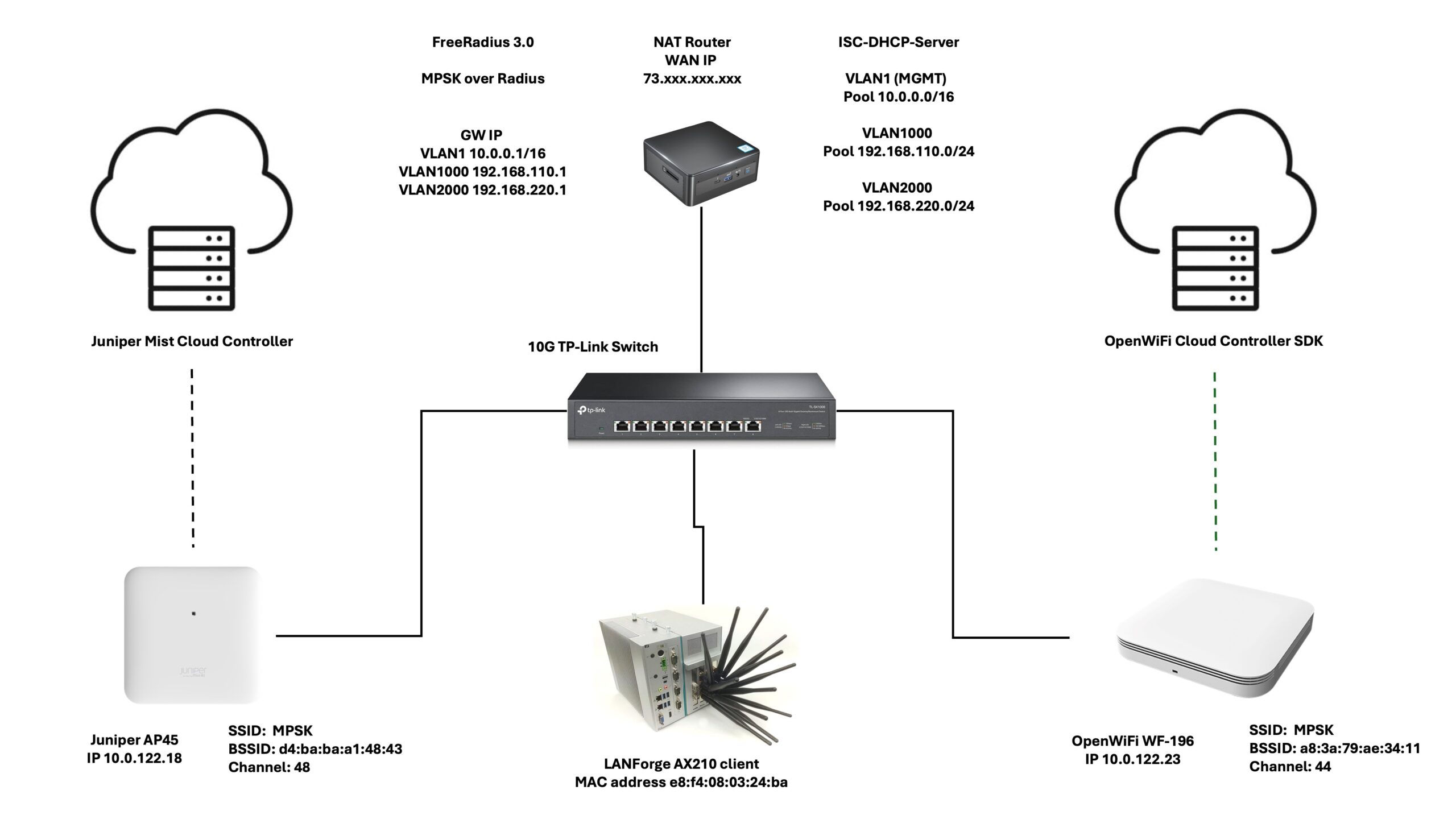
In today’s diverse networking environments, there’s a growing trend towards combining proprietary vendor solutions with open-source alternatives to achieve a balance of reliable performance and cost-effectiveness. This article explores this idea by demonstrating a Multi-Pre-Shared Key (MPSK) Wi-Fi solution using both Juniper APs and OpenWiFi APs, where authentication and accounting is managed through FreeRadius server.
The Network Setup
At the heart of the network, we have the 3.0 version of the FreeRadius server—an open-source solution capable of handling authentication for a variety of devices which I am running on my home NUC Ubuntu box, alongside a ISC-DHCP-Server to handle DHCP requests, and some iptables NAT rules to nat clients to the outside world . In this scenario, we’re looking at the Juniper AP45 and the TIP OpenWiFi CIG WF-196, both are configured through their cloud controller and added as clients within the FreeRadius’s clients.conf file.
# Juniper AP45
client a83a79a8367e {
secret = secret
ipaddr = 10.0.122.18
}
# OpenWiFi WF-196
client d4babaa1484 {
secret = secret
ipaddr = 10.0.122.23
}
For continuous roaming tests between these two APs, the Candela LANforge WiFi Roam test is employed. The test basically allows the user to construct a script that can run for a set amount of time or indefinitely. The operator can determine where, when, and how long the client should roam.


Configuring MPSK
The MPSK configuration requires minimal adjustments on the FreeRadius server. For each device, the MAC address and the PSK are entered into the users file:
# LANforge AX210
e8f4080324ba Cleartext-Password := "e8f4080324ba"
Tunnel-Type = 13,
Tunnel-Medium-Type = 6,
Tunnel-Private-Group-Id = 1000,
# Expected PSK for OpenWiFi using the tunneled password attribute
Tunnel-Password = 12345678,
# Expected PSK for Juniper in a Cisco AVPair attributes
Cisco-AVPair = "psk-mode=ascii",
Cisco-AVPair += "psk=12345678"
Notably, TIP OpenWiFi APs require the Tunnel-Password attribute, while the Juniper APs utilize the Cisco-AVPair attributes. The 2 different approaches show case how an homogenous ecosystem can be built by integrating proprietary and open source solutions with a universal authentication system like FreeRadius.
Mixed Ecosystem Benefits
The merger of TIP OpenWiFi and proprietary solutions like Juniper’s APs provides numerous benefits:
- Cost Efficiency: TIP OpenWiFi APs like the WF-196 are significantly more affordable than many proprietary solutions and can sometimes be the only realistic solution in industries with limited budget. A simple comparison of the two APs demonstrates why the open source solution might be a game changer for industries where budgets are limited.

- Flexibility: TIP OpenWiFi’s open-source nature allows for extensive customization and integration. The open source code allows for customizations that might not be available with the vendor locked solution.
- Innovation: Proprietary solutions often come with advanced features and robust support, while open-source projects bring community-driven innovation. As a member of the OpenWiFi community you have the opportunity to lead the development of new features on corner cases that the vendor might not be interested in developing.
Configuraing The OpenWiFi Controller: An SDK with a UI
The OpenWiFi controller stands out as an SDK (Software Development Kit) with a user interface, designed for developers and organizations to create their own user-friendly controllers.below we show a screenshot of the configs in a JSON file format. Not all fields have been expanded to not overwhelm the reader. Only the important parts that highlight the settings for the SSID and the RADIUS server.

The Juniper Controllers Configuration
Configuring the Juniper Controller was straightforward and uncomplicated. As someone who had never used it before, I felt as if I had been using it for years. Every configuration was where you expected it to be, and the transitions between steps were effortless.

Running the Test.
The brief movie below shows a wireless STA managed by the Canddela LANforge roaming between the AP45 (channel 48) and the WF-196 (channel 44). Two additional radios were utilized as sniffers to catch the traffic. An EAPOL display filter was employed to separate the 4-Way Handshake from the rest of the air traffic.
I did not get into the specifics of how to set up a FreeRadius server or the more in-depth aspects of the Juniper Mist MPSK setups because that was not the purpose of this article. If you need assistance with the issues listed above, please see my wonderful friend Mohammad Al‘s post at https://artofrf.com/2024/04/02/mist-mpsk-with-freeradius/.